Are you a victim of ransomware? Or have you been one in the past? If so, the following will help you understand what activities you should expect during the course of your ransomware recovery in the days following an attack.
Not only is ransomware completely indiscriminate in who it hits, but the perpetrators are unapologetic and relentless. In fact, their main goal is to cause maximum pain in order to extract maximum gain. Unfortunately, we see these attacks much too often.
Below is a timeline of what you can expect during a recovery process, followed by more detailed essential steps you should follow in a recovery situation. Be aware that these steps can vary from one situation to the next, and many of them can happen in parallel or in rapid fire succession.
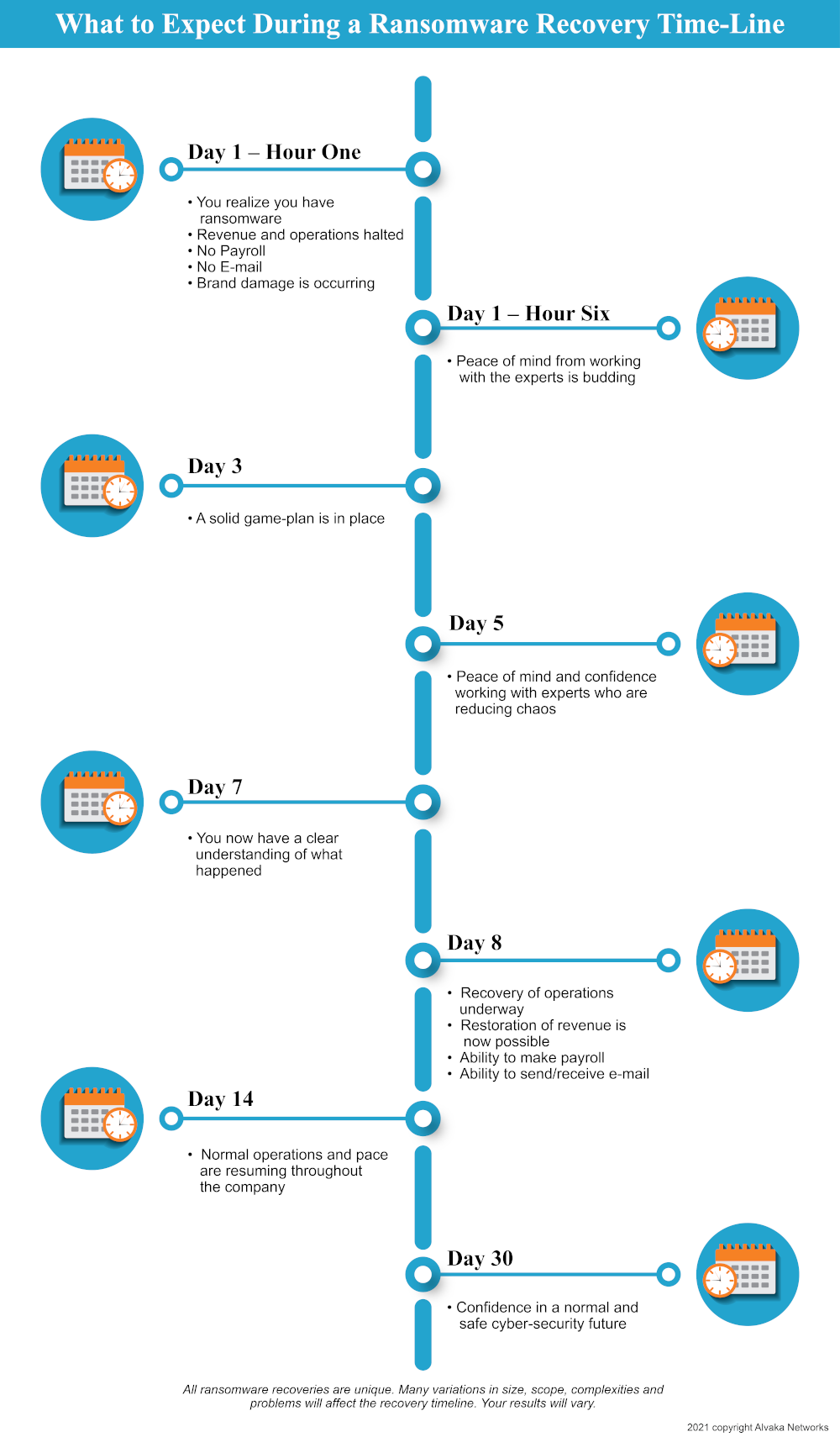
Ransomware Attack Recovery: What to Expect
1. First off, gather yourself up and take a deep breath. Every ransomware situation is a bit different, but your full recovery is likely. Expect an expensive, time-consuming and stressful set of processes. The following steps presume that you have already gotten a ransom notice and your system is completely held hostage. If so, time is of the essence, but acting rashly can cause more damage.
2. Your recovery team should start the examination process to assess your current situation: Identify which variant of ransomware you have and the initial extent of your damages.
3. Engage a lawyer. Not only are you facing a dire technical and business issue, but in many cases it can be a legal issue as well. Hiring the lawyer that will engage all parties involved in the recovery process can provide important legal protections via attorney client privilege. In the case that your records are subpoenaed, much of what is discovered here will be confidential.
4. Find out what your insurance covers. General liability insurance by itself is unlikely to have meaningful value; however, if you are lucky, it may cover some costs related to business interruption and ransomware recovery work. If you happen to have a cyber-breach insurance policy ($1 million or more) that covers forensics, recovery and remediation work, legal representation, public relations, business interruption, fines, and credit monitoring for individuals, you are likely in a better position than most to begin recovering from a horrible event such as ransomware.
5. Working with your entire response team, you will need to determine if it is necessary to gather forensic information. This information can play a vital role in developing the recovery plan. It might also be essential in meeting breach notification requirements, law enforcement inquiries, and more.
6. Keep quiet. Most firms keep the details of the incident very confidential for numerous business reasons. What you do decide to tell your customers, employees, investors, vendors, regulators, the press, etc., should be the result of a well thought out plan.
7. If the ransom amount is significant, you might want to consider hiring a ransomware negotiator. There are specialty firms that do this, and if needed, Alvaka can recommend one.
8. Determine whether or not you will pay the ransom. Deciding to pay will depend on the extent of the damage, the value of the lost data, the likelihood of a recovery without paying, and other variables. Understanding the extent and cost of the encrypted data is also essential to subsequent decision-making throughout the recovery process.
9. If the ransom is paid, how certain is the response team that the decryption will actually work? Though the encryption might have happened over a weekend, decryption is usually much slower and can often take up to a week. If you are able to negotiate and buy some time while you figure out your overall strategy, that can often be helpful.
10. Review your plan. At this point it is likely most—or all—of the above steps have been completed and your recovery plan should be critically reviewed by all stakeholders. These stakeholders include: you, your lawyer, the insurance company (if any), the forensics firm, the recovery firm, the negotiators, PR firm, etc.
11. Execute the plan with great vigor, speed and tenacity. This will be a long hard journey, with everyone working non-stop. Expect numerous daily conference calls during the recovery and changes to the plan, as new information is learned and new challenges are encountered. With commitment from your entire team, you will get results!
12. Create and implement a new cybersecurity plan to defend against future infection. Many victims don’t learn their lesson from the first attack and are doomed to a repeat infection because they refuse to execute the proper cyber defenses needed.
13. Scan and monitor your system constantly for possible artifacts from the original infection that were possibly missed in the recovery, or for possible new attacks from cybercriminals.
14. Make cybersecurity planning a part of your annual capital expense and operating expense budgets.
We hope this will be a valuable guide to anyone hit with ransomware, or provide insight to those who want to prevent an attack.


