Oli Thordarson, CEO of Alvaka Networks, begs to differ…
This is an interesting article I read in ZDnet, Cybersecurity: One in three breaches are caused by unpatched vulnerabilities, about software vulnerability patching. I found it interesting because I took some issue with the findings of the study. Let me grab some selected text to pick on.
“IT security professionals admit that one in three breaches are the result of vulnerabilities that they should have already patched” and “One in three IT professionals (34%) in Europe admitted that their organisation had been breached as a result of an unpatched vulnerability (higher than the average of 27%) according to a survey by security company Tripwire.”
I contest the above statistic. The article cites the survey as coming from Tripwire. Tripwire is a good company, with a good product you should all check out if you don’t use it. It is the survey responses of the IT professionals of whom I am very suspect, questioning how accurate a handle they have on how they were breached. Yes, lack of patching is likely the cause for at least 27% of the breaches, but I suspect the real number is double that.
This one is laughable…
“Finding the stuff that needs patching can be a challenge: 59% of respondents said they can detect new hardware and software on their network within hours, but it’s a difficult manual effort for many, with 35% saying less than half of their assets are discovered automatically.”
I would be impressed if 5% can detect new hardware and software within hours. The truth is, most IT professionals don’t have the slightest idea about what hardware and software is getting added to their network. How do I know? I have 37 years in the IT management profession and I have dealt with thousands of end-user companies. I have not yet found one that has a good inventory of their hardware and software, let alone an ability to know when something is added or deleted. Inventory management is one of the biggest unsolved problems for the IT professional, and it is no fault of their own. The tools to do so effectively don’t exist.
This is the biggest whopping lie by the survey respondents, or it just shows how naive they are.
“Just under half of companies said they aimed to deploy a security patch within a week, while over 90% of companies said that they would generally fix a flaw within a month. But nearly half of companies said they had to deal with less than 10 vulnerabilities a month; another 29% said they had 10-50 patches to apply every month.”
I have never seen a company that applies patches in a week. A more accurate statement would be, “If we are lucky we haphazardly apply patches over the course of the year, but we miss most of the patches and most of our systems.”
The paragraph goes on to say nearly half have to deal with less than 10 vulnerabilities a month. Clearly they have no idea what they are doing.
I will close with a snip of the graphic below. The most accurate portions of the graph are circled in yellow. The companies in the know, and with a mature patching process, are aware that there are more than 100 vulnerabilities each month; and if they have good discipline, staff, budget, tools and processes, they are a minority who get things patched. But in the real world, most are patching “None”, or they don’t know.
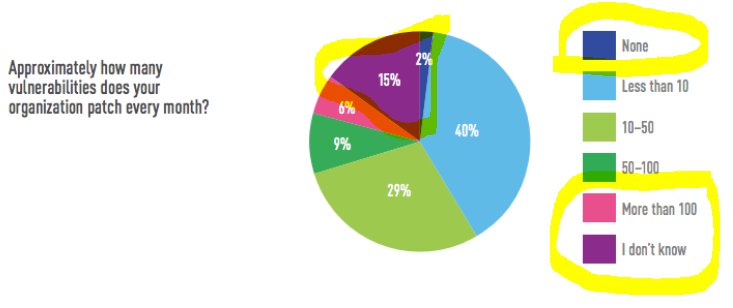
Note: This is a response to the findings discussed in “Cybersecurity: One in three breaches are caused by unpatched vulnerabilities.” Article originally published by ZDnet on June 4, 2019.

 Smoke testing is a term used to describe the testing process for servers after patches are applied.
Smoke testing is a term used to describe the testing process for servers after patches are applied.  This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.
This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.