Should you buy cyber breach insurance? Below are the top reasons why you should…#5 is the most important one!
In August of 2018, I shared an opinion about the value of cyber breach insurance. I was not very fond of it, at least not at the time given the typical insurance company terms vs. the typical cost of the risk at the time. Here is that opinion – Should I buy cyber insurance? A friend in the insurance business wrote a countering opinion we published. Here is his rebuttal – Read the reply to this blog from David McNeil He made some good points that made the value of cyber insurance better. I was partially altered in my opinion, but I was still not the strong advocate for cyber insurance that I am today. I will share my change of opinion.
The first paragraph gives away my opinion on cyber insurance. Let me share why it is an indispensable asset to purchase in today’s computing environment.
Why You Should Buy Cyber Breach Insurance
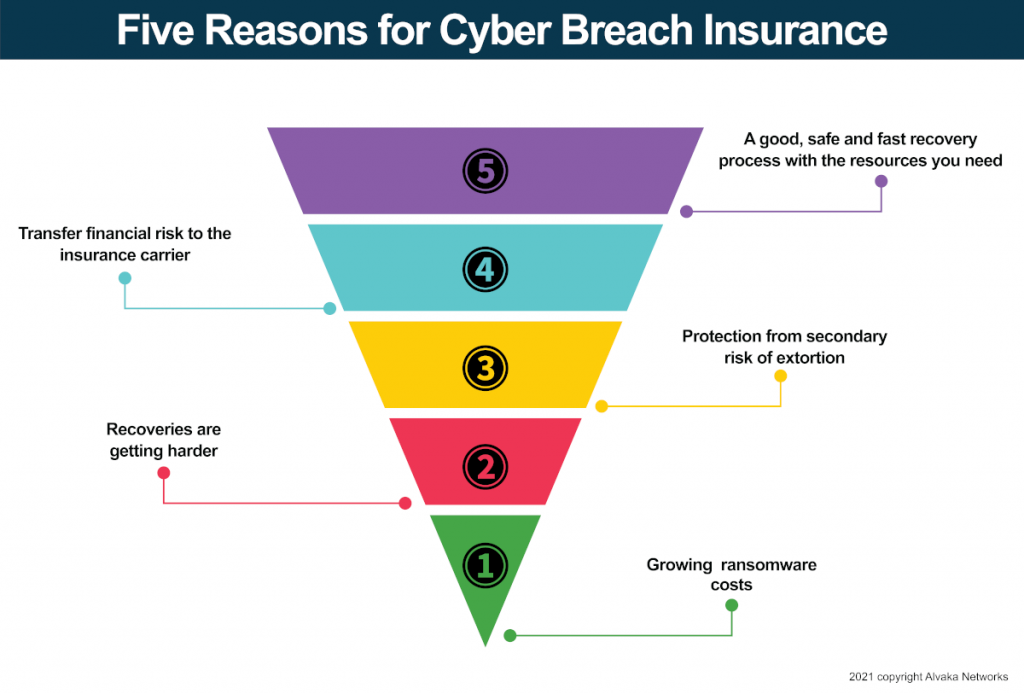
1. The trends are working against you. In the early years of ransomware, even a large $200M per year company would only get a ransom of $300-600. The ransomware threat actors did not know if they hit your grandmother’s PC or a large company. However, by 2018, they seemed to figure out how big the victim was and they priced accordingly. Typical ransoms for a company that size grew to $50-80k. Ransoms continued to rise, and by January 2020, even a company doing only $20M annually could expect a $50-100k ransom. Then came the COVID-19 lockdowns and the work-from-home mandates. Internal and external IT staff were ordered to hastily deploy WFH solutions. Not much regard was typically given for security which created an explosion in ransom opportunities for the crooks. By May of 2020, a $50-100k ransom tripled to $200-300k. Unfortunately, the next few months did not get better, and by September 2020, we were seeing $1-2M plus ransoms. A couple of months later I saw my first $20M ransom.
2. It is harder now to recover. Since 2018, you can now expect the ransomware gangs to delete your backups, too. They get into your system, exercise patience, and learn everything about your system while you do not even know they are there. When they decide to take down your company they do so with a plan. They usually hit at the start of a weekend or a holiday when they are less likely to be detected. This gives them the time they need to make sure they can execute the plan in full. That includes deleting all your backups as well as encrypting all your data.
3. They will extort you. Getting a demand to pay a ransom to get your data back is bad enough, but in the weeks or months the threat actors were in your system getting ready to hold you hostage, they were also downloading all your valuable data. So if you are one of the lucky ones that can restore from an off-line backup to return to business, the ransomers will tell you, “Pay up anyway or we will publish all your confidential information out to the Internet and Dark Web.”
4. Transfer risk to the insurance carrier. Yes, the traditional role of an insurance carrier provides you the opportunity to get the insurance company to pay if you have a loss. That remains true today, but make sure you get enough. In the past, $1M in coverage was more than adequate. Most losses used to be well under that. Today, expect any loss to be at least $500k to $1M. If you have one or two weeks of business interruption, which is likely, you can do your own math as to how big your claim will be. Make sure you look at the terms of your insurance. You want insurance that pays for:
a. The ransom
b. Forensics
c. Ransom negotiation
d. Legal representation
e. Ransomware/breach recovery
f. Public relations
g. Fines and breach notification
h. Business interruption
5. Follow a sound ransomware recovery process with the right resources. The most valuable component of cyber insurance these days is not the payment for the losses you incur. It is the experienced process the insurance company typically brings to the recovery process. One criticism I can level against most of the insurance carriers is that they are bureaucratic and slow in most cases. This is particularly true over the weekend or holidays when most companies are hit. If one or two of the insurance companies can fix this problem, they will be providing vastly improved value to their clientele. Many victims opt initially to pay for recovery services out of their own pockets so they can start recovering immediately. They then work with the insurance company during the week to get them on board. So what is this process the insurance companies bring? It is access to the resources you need to solve the problems of sub-bullets a. through h. in bullet #4 above. Insurance companies have resources to recommend for a successful for recovery. Those resources start with a cyber-breach experienced law firm. You need this type of firm to provide guidance and attorney/client privilege if and when legal issues arise. They will recommend top-notch forensics companies like Kroll so that the cause and extent of the breach can be determined. They pay for experienced ransomware negotiators like Coveware to bring down the cost of the ransom. Most companies end up having to pay the ransom even when they do not think they do at first. Then, you will need a great ransomware recovery firm like Alvaka Networks. You need a team of engineers experienced in the tasks that are required to clean up the infected mess and execute a statement of work based upon a containment list so the threat actors do not start reinfecting the system as it is recovered. Yes, reinfections are common.



 Smoke testing is a term used to describe the testing process for servers after patches are applied.
Smoke testing is a term used to describe the testing process for servers after patches are applied.  This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.
This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.