The last two years have been a bloodshed for cyber breach insurers. From 2016 through 2019, the payouts on each dollar of cyber breach insurance billed ranged from $0.43 to $0.48. In other words, loss ratios were 43% to 48%. Losses from 2020 and 2021 have ramped up considerably, partly due to extra vulnerabilities induced by COVID-19 related work-from-home mandates, and also because the ransomware gangs are getting better at what has become a bigger business than global illegal drug smuggling.
These big losses are causing many cyber breach insurers to exit the market. Others are limiting the amount of overall coverage, limiting payouts by breach category, upping the deductibles or retentions, adding exclusions, demanding greater cybersecurity preparedness, and getting more selective about who they insure. This article focuses on the new demands from cyber breach insurers with regards to the more detailed self-attestations.
Alvaka has become more of an ardent proponent of cyber breach insurance over the past couple years. The years prior were bountiful years for the insurers, as the payouts were relatively low. Even at the higher insurance rates of 2022, it is one of the best deals you can get in insurance. After all, your business is more likely to have an expensive ransomware attack than burn down, be hit by a natural disaster, etc. A ransomware event is every bit (or more) damaging than the spectacular traditional losses. One key reason is that ransomware will likely hit every facility and corner of your business operations, not just a single physical geographical location. And recovering from ransomware can be just as expensive (or more) as constructing a new building. The losses we have seen hit businesses in the past two years are colossal.
We will look closer at a sample application from Tokio Marine, one of the key cybersecurity insurers, which will be similar to most of the applications we will see for 2022. If you are not already familiar with these applications, you will be surprised by the technical nature of the attestations they expect you to make. Even for IT department professionals, many of these questions are going to be difficult to answer. You may have to do research to get educated on the full meaning of these questions, and will likely need to reference system documentation or inspect your systems to answer all the attestations accurately.
With the heavy insurer losses over the past two years, we believe not answering the questions accurately and honestly can be a real threat to you in the future when you go to make a claim, as coverage could potentially be denied. It will also take discipline during the coverage period to stay true to what you promise on that application. Staying current on all your IT system management and cybersecurity practices is the most important task you need to adhere to in order to prevent a ransomware breach and possible loss of coverage.
We will highlight sections of the cyber breach insurance application below with some brief commentary. You can see the full applications on the Tokio Marine Cyber Liability page.
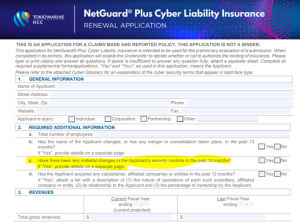
Cyber Breach Insurance Policy: General Info
This first section (below) looks standard and relatively harmless, but question 2c should make us all scratch our heads and think hard before offering a flippant answer.
Cyber Breach Insurance Policy: Managing Records
We don’t know too many organizations who have a high exposure from question 4b below, but for everyone else, questions 4a and 4c do create a significant risk of exposure.
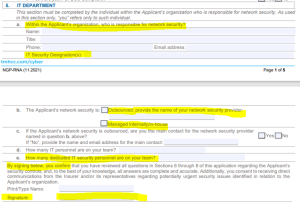
Cyber Breach Insurance Policy: IT Department Info
Question five below is where things start getting real. They ask “who is responsible” and for the IT security credentials of the person responsible. Question 5b is likely to require checking off both boxes, and 5e may likely determine whether your team has the cybersecurity gravitas to properly protect your network. And then there is the signature attesting to what you are promising.
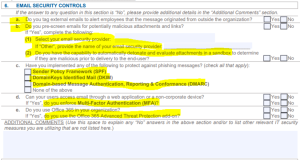
Cyber Breach Insurance Policy: Email Security Controls
Email is a common entry point for the bad actors to establish the first foothold into your network. It is no surprise that the insurers want to know what you are doing to address this risk. From our experience in regards to question 6a (below), we don’t see many companies doing this. For 6b, the best way to do this is to outsource to a reputable service provider; doing this in-house is usually inconsistent at best. For 6c, no matter what you are told, the honest answer is “none of the above”…we see very few companies conforming to these solid email security practices. MFA and O365 Advance Threat Protection is becoming more common, but anecdotally, we see it at less than 50% of the companies we come in contact with.
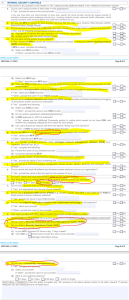
Cyber Breach Insurance Policy: Internal Security Controls
Almost the entire internal security controls section below is highlighted because it is so vital. In nearly every company, we see the majority of these items overlooked or inadequately managed. MFA (7b) is still woefully rare and most companies are still relying on legacy antivirus software (7e and 7f). EDR is where companies need to migrate, while ensuring that AV is installed on all systems and up to date. Often, we see AV not deployed to all systems and in systems that have it, not all are up to date. Way too often, regular users have the same rights as the System Administrators (7l), which is very dangerous.
Also dangerous and a huge vector for successful attacks is not having good patching practices (7m). If you fail to patch regularly, you will become a target. Most patches can be installed in a 30-day window, but on occasion, you will need to patch immediately for what are known as zero-day threats. You need to have system monitoring in place for both performance monitoring and threat monitoring (7s and 7t), as the two work together. Performance monitoring is often an early tripwire that something is amiss that is the beginning of cyber breach. SIEMS collect event logs to also warn you of impending danger, or to discover what happened after-the-fact. For legal and technical reasons, it is vitally important to know what happened, even post breach. Finally, you need to run vulnerability scans against your network on a regular basis (7u).
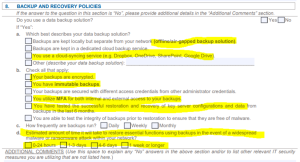
Cyber Breach Insurance Policy: Backup & Recovery Policies
The next section we will look at is Backup and Recovery Policies (below). Integrity of backups is essential to recovery if the methods of protection above fail; and they do with much regularity. One breakdown in the process can lead to a breach. The past two years have been the birth years for air-gapped backups (8a). The bad actors can now delete all your backups when they breach your system. They seek to create maximum pain and suffering for you so they can extort big ransoms and denying you an ability to recover achieves this goal. And don’t think you are safe with cloud synching services; all too often we see those encrypted, too.
There is a time for YOU to encrypt your data in case it falls into the wrong hands, when backups are transmitted or stored (8b). Backups should be encrypted as part of the backup process. Immutable backups are somewhat new and though we don’t see much proven use in commercial practice, we expect that will change soon enough. As stated above for system access, MFA should be required to administer your backups, although many providers are still working to add this functionality to their software. Regarding question 8d, there is something called RTO (Recovery Time Objective) and RPO (Recovery Point Objective). RTO is the time it will take you to recover. If you only have cloud storage for multiple terabytes of information, it can take a week or more just to download your data from the cloud. RPO determines how stale your backup is when you restore. If you backup every night, when you restore, you will only lose data from the prior 24 hours. If your backup is a week old, you might lose a week’s worth of data.
Cyber Breach Insurance Policy: Phishing Controls
Section 9 relates to phishing controls. We have seen more than $750,000 lost on fake wire transfers. The questions below are somewhat self-explanatory about best practices, but the number one trick we see is when the bad actor compromises a company’s email system and poses as a vendor. As “the vendor” they send an email to the company saying they have changed banks and attach new (fraudulent) wire transfer information. There are many more tactics when it comes to phishing, as the bad actors are very creative.
Cyber Breach Insurance Policy: Loss History, Notice & Certification
The policy application concludes with some simple check boxes and important fraud warnings. This is the notice that the attestations are part of the basis for a contract, and it is the signer that is making personal promises as to the accuracy and honesty of the application.
We know this can be very overwhelming, but the good news is that good cybersecurity service providers (like Alvaka Networks) can help you through the process of complying with the increasing demands of the insurance companies. Nobody wants to incur the wrath of a bona fide security breach. Complying with the requirements as set forth by the insurance companies will improve your security posture tremendously. Let us know what we can do to help speed you along a secure compliance path.
We are available 24×7 to assist you with any of your ransomware needs…contact us at (949) 428-5000 or info@alvaka.net.
[/fusion_text][/fusion_builder_column][/fusion_builder_row][/fusion_builder_container]






 Smoke testing is a term used to describe the testing process for servers after patches are applied.
Smoke testing is a term used to describe the testing process for servers after patches are applied.  This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.
This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.