The following is a guest blog written by Ciaran Foley of XeneX. Ciaran discusses the current and future state of cybersecurity, including the big business of enterprise-scale ransomware operations.
As a Corporate Executive or Board Member, you may never have heard of Ryuk. However, your cybersecurity team likely has. Ryuk is software specifically designed to target technology systems in the enterprise and hold them hostage (enterprise-scale ransomware). Ryuk ransomware has been in steady development since its release, operated by a Russian criminal organization known unofficially as “Wizard Spider.”
Based on the name alone, it sounds like an entertaining premise for a lightweight fictional thriller. But don’t let the organization’s puerile moniker fool you: since Ryuk appeared on the scene in August of this year, Wizard Spider has successfully victimized over 52 organizations, rewarding the criminal group with close to $10 Million in ransom (in current Bitcoin value).
A disturbing message presents itself to each victim:
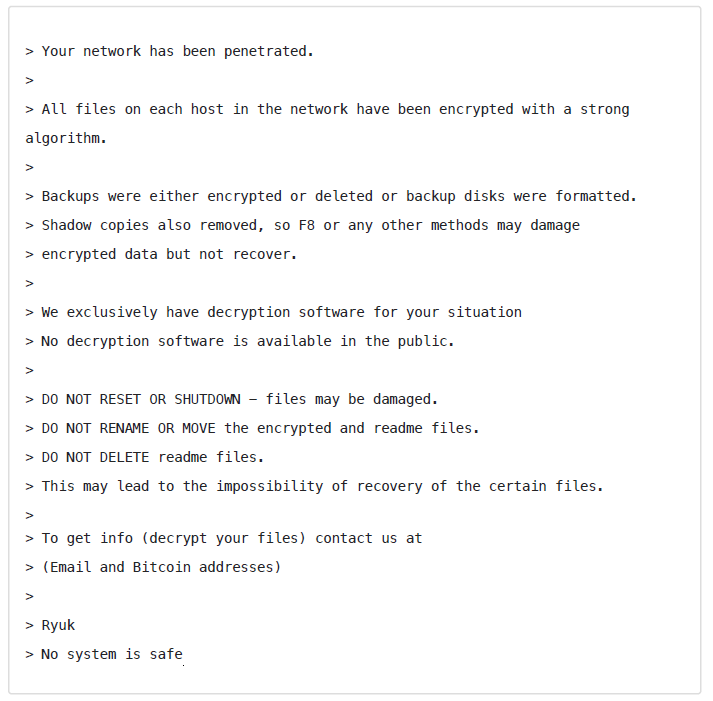
While this is one of the most financially successful attacks to date, Ryuk is only one example of many. Big-game hunting (as enterprise-scale ransomware operations have come to be known) is big business and it’s only growing. In 2019, 80% of I.T. leaders polled indicated they expected a successful cyberattack of their enterprise within the next year.
True to form, in 2019, a sample of the largest attacks revealed criminal spoils of over $75 Million. The same year, 205,280 organizations submitted evidence that they had been victims of a ransomware attack (up 41% from 2018).
Now, some of you may be sitting comfortably reading this within the confines of a multibillion-dollar multinational. These figures may fail to elicit a feeling of discomfort. They may even appear minor. This is understandable. The largest organizations may feel well prepared with sufficient backups, good training, and the best security professionals at their disposal.
What follows may challenge that confidence a little.
First, let’s look at a few obvious consequences of a given attack on any organization:
- Halting Business Immediately: Ransomware cripples an organization, encrypting data and rendering it completely inaccessible. In extreme examples, the result can be much worse. A recent cyberattack is the first credited as directly responsible for a death. Even with the proper backups and protocols in place, enterprises can expect significant effort to recover, if they can at all.
- Lost Opportunity Costs: Today’s business doesn’t wait. Global business is unforgiving. An attack causes havoc within an organization, potentially disrupting time-sensitive coordination with suppliers, partners and clients.
- Permanent Loss of Data: Even if the keys to the kingdom are recovered, there is no guarantee something has not been destroyed along the way. The risk of permanent loss of data during and after an attack is significant. “Loss of data” is a clinical and emotionally devoid way of describing what is really at stake. This represents the loss of years of work, accrued value, and in some cases, even information critical to life.
- Corporate Reputational Damage: Given the frequency of cyberattacks, it is natural for companies and the general public to become desensitized. However, the stakes are being raised and it won’t be long before the perspective of “it’s just something we have to deal with” is replaced with outrage, regulation, and severe consequences. Meantime, the reputational damage cannot be overstated, especially in those cases where corporations are seen as irresponsibly letting loose the personal and sensitive data of clients, partners, and employees. According to Paige Boshell of Privacy Counsel, data breaches are frequently attributed to a lapse in management or lack of attention to consumer privacy, rather than as the result of the organization being the victim of an attack. This raises the stakes even higher.
 These are just a sample of potential outcomes. For the smaller company, any one of these consequences alone can prove fatal. In fact, an estimated 60% of small companies hit by a successful cyberattack close within six months.
These are just a sample of potential outcomes. For the smaller company, any one of these consequences alone can prove fatal. In fact, an estimated 60% of small companies hit by a successful cyberattack close within six months.
In Q4 2019, of those that had the means to pay their ransom, Coveware reports the average payment to release hostage data was $84,116 (double the previous quarter). In December of 2019, it increased to $190,946. Some victims even faced millions of dollars in custom ransom demands.
The trend is easy to see and it poses a serious issue for a small and medium-sized company lacking deep financial resources. But what of the well-heeled enterprise? Despite its ability to absorb more of the costs of such attacks (and arguably, its ability to defend against them), the news on this side of the ledger is still not very encouraging.
The game we are witnessing is just the beginning. It’s “low-hanging fruit” stakes. Proof-of-concept. Easy pickings. Encrypt and collect a few dollars. It is lazy.
One need only glance at the global threat landscape and the opportunities criminals are leaving on the table today to understand what they may be back for tomorrow.
Consider how the environment is changing:
- Increased Interdependency: Organizational reliance on 3rd parties has extended risk for every organization. Each is only as secure as its closest suppliers.
- Increasing Speed: Attacks are happening faster. Last year, researchers at security firm Sophos set up “digital decoys” in ten locations worldwide, exposing them to potential attackers. It took less than 60 seconds for attacks to begin against the decoys, with the first login attempt clocked at 52 seconds. Once discovered, each decoy then registered a barrage of attacks (13 login attempts per minute). In just 30 days, one site recorded almost a million attacks. The typical security team simply cannot keep up without the right technologies to aid them.
- Global Corporate Competition: It’s a fierce world. From nation-states to large multinationals, there has never been a more opportune time to cast fishing nets far and wide to obtain competitive intelligence, steal intellectual property, mine data, steal customers and disrupt. It doesn’t take much imagination to understand that the same tools criminal enterprises are using to drain a bank account can be used to drive a competitive advantage.
- Politics and Warfare: From radicalized organizations seeking to establish and maintain influence to activists attempting to create change and nation-states exercising cyber warfare as the next theater of combat, each scenario brings with it significant risks for the enterprise.
- Technology Advancement: The degree of technical sophistication involved in the discovery and exploitation of vulnerabilities is light years ahead of where it was just a decade ago. Distributed attack botnets, machine learning, AI, blockchain-powered distributed DNS—there is no limit to the scale and speed of potential attacks from all directions.
- Democratization of Technology: From technically sophisticated criminals to the most amateur of hobbyists, all have benefitted from the democratization of operating systems, toolsets, and kits aimed at hacking. The very same culture that has informed and trained those attempting to create a semblance of security is also being actively exploited by those seeking to destroy it for their own gain or pleasure. Unfortunately, their job is becoming easier by the day.
- Criminal Business Models: Incentives are increasing. Everyone from the existing criminal to the rank amateur is trying their hand at getting a piece of the pie. From crypto-mining malware to phishing for private information resale, to ransomware, bits are rapidly converting to currency. Cybercrime is just getting its legs. New business models empower bad actors by licensing robust cloud-based attack subscription services that have emerged. Criminals can now access their (your) money and information faster than ever before.
- Money On The Table: Today’s attacks are crude compared to what we may see soon. Consider how a typical large or medium-scale enterprise generates, distributes, and stores value:
- Board of directors intelligence
- Corporate strategy
- Legal intelligence
- Private employee information
- Industry contracts
- Marketing channels and technologies
- Platforms
- Customer behavior data
- Internal operational data
- Contracts and pricing
- Targets and prospects
- Bank accounts
- Hardware assets and manufacturing capability
- Bandwidth and network resources
- Software
- 3rd party systems
- Intellectual property
- Research and development
- …and more!
Imagine a near future in which perpetrators of cyber-attacks become several orders of magnitude more sophisticated and patient. Instead of attacking enterprises for simple payoffs, a type of 3D chess is played. Advanced persistent threats perform reconnaissance to identify weaknesses that allow criminal cartels to carefully and deliberately exploit any number of these elements to:
- Influence and extort individuals
- Leverage aspects of the business for their own ends
- Influence and interfere with business operations
- Carry out nefarious activities using company platforms and resources
- Manipulate the business affairs of organizations, individually and collectively
- Leak and sell sensitive and confidential information for profit
- Develop competitive technologies
Today, cybersecurity can be a tough sell. CISOs are being asked to do more with less. Budgets are tight. Cybersecurity involves so much more than just the right technology: it is an active process that must involve everyone inside the organization. Taking the time to become informed about the current and future cybersecurity state at the Board and Executive level has become more essential than ever. As the stakes grow, so too may the realization that the ultimate ROI of proper cybersecurity may simply be the opportunity for us all to remain in business.



 Smoke testing is a term used to describe the testing process for servers after patches are applied.
Smoke testing is a term used to describe the testing process for servers after patches are applied.  This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.
This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.