Ransomware, first seen in 1989, has grown into a one of the largest criminal business industries worldwide, accounting for a total of $20 billion in damage costs in 2020. First starting with criminals developing their own codes to use for attacks, ransomware has evolved into a sophisticated industry that becomes harder and more resource-intensive to identify and defend from. Things such as ransomware-as-a-service programs, which were never thought imaginable, have become reality.
 Additionally, new ransomware variants are being created at a rate faster than ever before – making it more challenging for companies to remain proactive on their own. As a result, victims are finding it increasingly more difficult to identify which ransomware they have been hit with in order to start addressing it. Now, every 11 seconds, a business is victim of a ransomware incident. These numbers will only continue to worsen as cybercriminals find new and intelligent ways to bring companies to their knees.
Additionally, new ransomware variants are being created at a rate faster than ever before – making it more challenging for companies to remain proactive on their own. As a result, victims are finding it increasingly more difficult to identify which ransomware they have been hit with in order to start addressing it. Now, every 11 seconds, a business is victim of a ransomware incident. These numbers will only continue to worsen as cybercriminals find new and intelligent ways to bring companies to their knees.
Having valuable and reliable ransomware resources and information can make a huge difference in the ransomware recovery process. We have made it our mission to be a source of information for individuals and businesses by providing the most relevant resources and answers to the most common questions around ransomware prevention and recovery.
If you have been a hit by ransomware, one of the first steps in the recovery process is identifying the type of ransomware that you are dealing with. But how do you do that? There are many free ransomware detection programs available that are both reliable and easy to use, including ID Ransomware.
Identifying the Ransomware – Your First Step
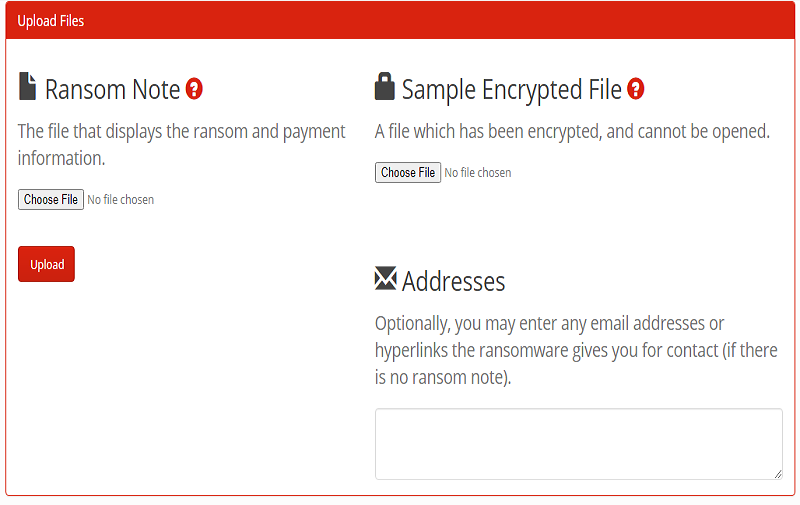
ID Ransomware is a simple yet highly efficient tool that comes free of charge. Users visit the ID Ransomware website and simply upload the ransom note and payment information along with an affected encrypted file that cannot be opened. If there are any email addresses or hyperlinks that the ransomware has given, users can upload those too.
Once the information has been uploaded to the ID Ransomware website, the service quickly gets to work identifying nearly 1,000 different ransomwares types. Once the ransomware is detected, ID Ransomware lets users know if there is any known way to decrypt your files. If your results return multiple types of ransomware, they will be ranked by how many matching signatures they have for each type.
Next Steps in Recovery Process
Once the ransomware has been determined and the user knows exactly what they are working against, they can then begin to formulate an effective plan to resolve the issue. This plan will look different in every situation, however you can generally expect common essential steps in the process.
In a world where our lives become more and more intertwined with technology, your cybersecurity is perhaps one of the most important things you can safeguard.



 Smoke testing is a term used to describe the testing process for servers after patches are applied.
Smoke testing is a term used to describe the testing process for servers after patches are applied.  This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.
This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.