Impact of Cloud Landscape on Incident Response
Cloud incident cases differ from standard incident cases because of the different technology concepts. Currently, malicious actors in cloud environments have it easy because many aspects of the cloud landscape are unknown. The cloud is considered low-hanging fruit for several reasons: Cloud environments are dynamic and transient so traditional incident response methods don’t work within the cloud. Cloud environments are elaborate and convoluted because they use a diverse range of tools and applications that can be hosted across many cloud service providers (CSPs). This presents challenges when trying to comprehend the full scope of a situation in the cloud.
Any incident response method, first and foremost, requires data collection and acquisition of evidence. With standard methods, one can simply just look through logs and data files in order to collect the evidence needed. However, a breach in the cloud means reviewing ten times more data and working with impermanent evidence/material.
Working within cloud environments requires CSPs, companies, employees, and clients to have a general understanding of the shared responsibility model. This model is a general framework for protection and regulation and defines the joint duties of CSPs and clients for ensuring comprehensive cloud security.
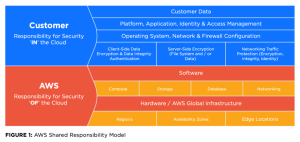
Read more about the AWS Shared Responsibility Model HERE
These days, the majority of organizations handle their business within the cloud and utilizing the cloud offers many benefits. What many organizations don’t realize is that they are the ones responsible for IAM (identity and access management) and security controls. The CSPs provide built-in security, but in reality, these security controls require activation and proper configuration by the organizations that use them.
In the event of a cloud incident, an organization that hasn’t configured their data may not have access to the critical evidence needed to carry out an investigation.
Cloud Threat Actors are Thriving
As of now, threat actors don’t have to try hard in order to be successful. Ideally, cloud environments should be properly configured so that data is readily available and preserved. Also, IAM should be effectively managed and CSP security controls should be manually activated. However, as of now, 99% of organizations struggle with cloud breaches because of misconfigurations and improper IAM policies. Cloud breaches have been increasing at an alarming rate and researchers have found that threat actors have many “low hanging fruit” to choose from. Improper configurations account for 70% of the identified cloud security incidents. Misconfigurations grant threat actors easy access into a cloud environment without needing to use techniques or exploit vulnerabilities; It’s essentially the same thing as leaving the key right in front of a locked door. Compared to complicated ransomware extortions, threat actors breaching cloud environments just need to destroy or steal sensitive data and credentials in order to make money.
Make a Threat Actor’s Job Harder
The whole idea of IT security is to make a hacker’s job that much harder. As of now, a cloud hacker’s job is easy and many bad actors don’t need to use any advanced techniques to breach cloud environments. To safeguard their assets from cloud breaches, organizations should prioritize educating their employees about cloud technologies and properly facilitate IAM; This ensures that access to an org’s cloud environment is limited to authorized and authenticated personnel only, enabling them to conduct business securely. Proper setup of logging/monitoring can help in detecting breaches or security issues faster. The importance of cloud incident response playbooks and the mitigation of cloud risks has become increasingly vital, now more than ever.







 Smoke testing is a term used to describe the testing process for servers after patches are applied.
Smoke testing is a term used to describe the testing process for servers after patches are applied.  This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.
This is a basic cost calculator for you to compute your typical monthly cost for patching your servers, PCs, laptops, tablets and associated application software. It also forms the basis for you to begin calculating your Return on Investment for software patching, or for comparison with alternatives to the manual process of patching operating systems and application software—such as Patch Management as a Service, also known as Vulnerability Management as a Service.